Have you been breached?
Digital Era Group can help you now.
We have the knowledge and power it takes to manage complex security breaches and protect any type of organization from compromise. Our team will work together with your organization to quickly gain visibility into vulnerabilities in your network and environment,
with unmatched effectiveness, minimal system impact
and zero-day prevention, allowing you to get back to
what matters most.
For urgent contact:
Phone: 1 (786)-621-8600
Email: info@digitaleragroup.com
WhatsApp: 1 (786) 621-8600.
To learn more about DigitalEra™ expertise in Breach Response, click here
By clicking Submit, I agree to the use of my personal data according to the DigitalEra Group Privacy Notice. DigitalEra will not sell, trade, lease, or rent your personal data to outside parties. I understand the personal data I provide may be transferred outside of my country of residence to fulfill my request.
When a cyberattack occurs …
It’s crucial to act immediately. After a breach, it is vital to decrease your down time and reduce any direct and indirect costs you will face. Our Incident Response service is designed to find the root cause of the attack, discover evidence, and remediate the problem thoroughly and efficiently.
Incident Response Process
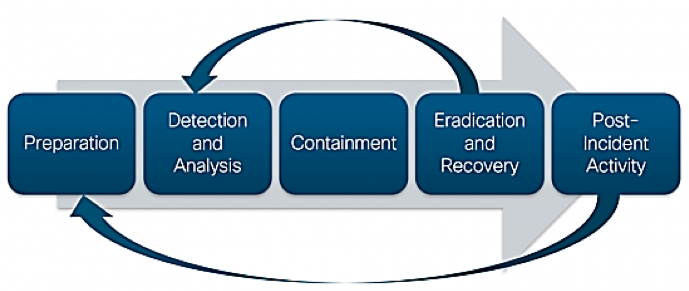

Detection and Analysis
The identification phase is to determine nature of the incident, the depth of the compromise, its source, and its success or failure.

Containment
Containment often happens concurrently with identification or immediately following. Systems are removed from production, devices isolated, accounts locked down — the bleeding stops.
.

Eradication and Recovery
Removing and remediating damage discovered in the identification phase. This is normally done restoring systems from backup and re-imaging workstation systems.

Post Incident Activity
One of the most important parts of incident response is to learn from the incident. After a major incident, security measures must be improved to prevent repeat occurrences.
